FAQ

FAQ
SEC-TPM™
A trusted platform module (TPM) is used to secure a device. It provides a unique device identity that cannot be changed (a root-of-trust), creates and stores encryption keys, and provides boot measurements to verify that software is authentic. It follows a standard maintained by the Trusted Computing Group (TCG). It is the foundation for device security can be used to implement fundamental security features like:
- Secure boot and updates
- Cryptography
- Key and certificate management
- Secure storage
- AI model protection
- Secure cloud integration
- A dedicated chip (called a Discrete TPM or dTPM)
- Firmware (called an fTPM)
- Software, anchored in the chip
A firmware TPM (fTPM) is a software-only version of a hardware TPM. It typically runs on the main CPU instead of being a discrete chip. Therefore, fTPMs can perform certain functions better than discrete TPMs. However, fTPMs do not have the tamper protections and resistance inherent to discrete TPM chips, unless the main CPU has such abilities. fTPMs also have the ability to be more quantum resistant since they can be updated in the field unlike discrete TPMs. Another advantage is provisioning the fTPMs can be done late in the manufacturing cycle to further improve the security of keys and certificates.
SEC-TPM™ is SecEdge’s firmware TPM that is secured using a hardware isolation technology known as the Arm® TrustZone™. TrustZone is a hardware enforced, domain separation technology that is available on most Arm-based processors. SEC-TPM also includes a provisioning service that enables secure injection of device credentials into SEC-TPM. The provisioning service also includes the ability to “activate” SEC-TPM.
A firmware TPM has the following advantages:
- Crypto agility – A firmware TPM can be upgraded in the field; a hardware TPM no longer secure if its supported encryption algorithm becomes obsolete.
- Performance – A firmware TPM runs in the device’ powerful processor versus on a separate chip, removing a key performance bottleneck. A firmware TPM enabled device can perform between 2x and 15x better than a device using a discete TPM.
- Security – A firmware TPM is anchored in the processor, while a hardware TPM is exposed can be physically tampered with or accessed.
- Cost – By using a firmware TPM, a developer can save the hardware cost of a TPM chip. In addition, additional costs of designing in the chip, maintaining inventory, and engineering design changes, can be avoided.
- Provisioning – A firmware TPM can be provisioned an activated post-assembly. A hardware TPM requires a secure manufacturing facility.
Most Open Source fTPM solutions exist as reference platforms only. This means that the customer or the device maker has to do a lot of work to ensure that it works as desired.
In addition, the device maker is left to figure out how to provision such open-source solutions and must invest in setting the process and infrastructure to do so. SEC-TPM, on the other hand, delivers a complete solution and a provision and activation service. This reduces the time to market and total cost of implementation.
SecEdge collaborated with NVIDIA to deliver a device security solution for the Jetson platform. The fTPM feature is available in the Jetpack for customers who have deep in-house security expertise and would like to develop their own custom solution for a specific product line. SecEdge introduced SEC-TPM as a turnkey solution including device security (with fTPM), AI model protection, and provisioning. It supports the requirements of most of NVIDIA’s customers.
EC-TPM is fully compliant to TCG 2.0. Our vendor ID is
: 0x5ECE.
While the SEC-TPM firmware may be present on the device, it needs to be activated in order for the security to take effect. This involves binding the SEC-TPM to the CPU silicon. This process is known as “activation.” Activation can be conducted at any point once the software is present. It can be done during manufacturing at the ODM, or later when installed at the customer. Typically, the device must connect to SecEdge’s activation server to complete the process. However, in specific instances, SecEdge will provide alternate activation methods in the case of “unconnected” production facilities.
FAQ
SEC-VPN™
SEC-VPN™ delivers a unique secure connectivity solution, covering a large variety of chip platforms, addressing Edge and IoT security requirements, and supporting industry standards, regulations and forums. It is an IoT VPN using IPSec to connect client software on the IoT device to endpoint software in the customer’s backend. In addition, it includes a control software to oversee and manage the endpoints.
SEC-VPN™ is a muti-tenant, scalable IPSec solution, providing secure connectivity to edge devices. The solution has three software components:
-
- MicroEdge™, a Linux device agent installed in the device to manage IoT VPN;
- NetEdge™, the IoT VPN termination point installed in a VM and connected to the backend application; and,
- ControlEdge™, central security and control management software, accessed via APIs (if hosted in the cloud) or installed on-premises (Kubernetes environment).
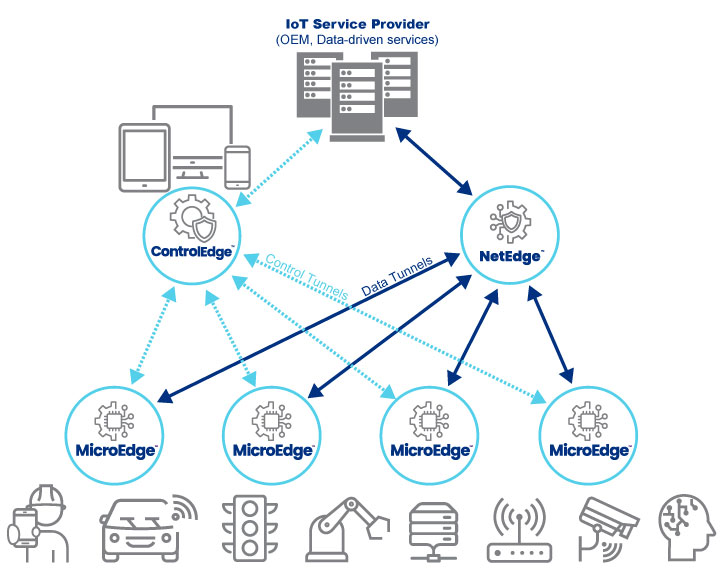 *NOTE: NetEdge™ was formerly branded as CloudEdge™.
*NOTE: NetEdge™ was formerly branded as CloudEdge™.
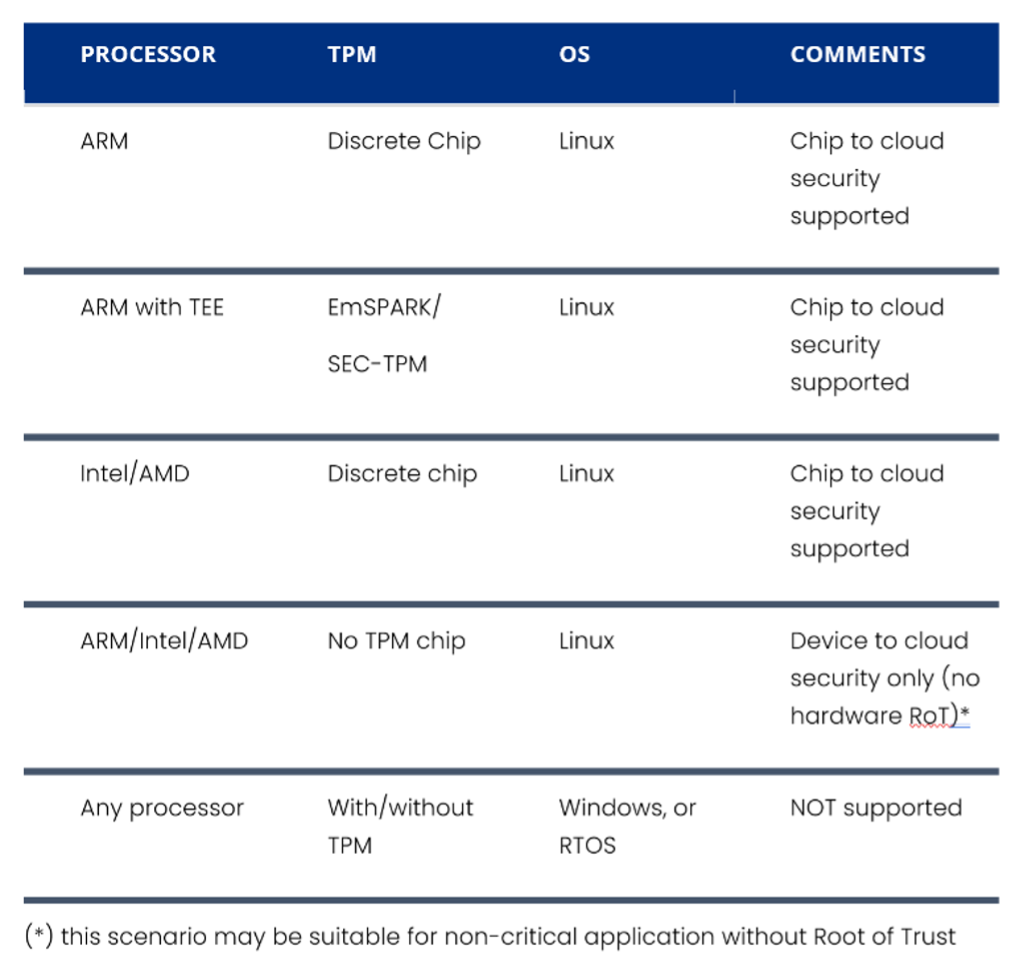
Any Linux device can be integrated with SEC-VPN™. If the device is equipped with a hardware RoT (Root of Trust), SEC-VPN will provide chip-to-cloud security. Both Arm processors and Intel processors with Linux OS are supported. The RoT can be a discrete TPM or a solution implemented in the Arm TEE (for example, SecEdge’s SEC-TPM™).

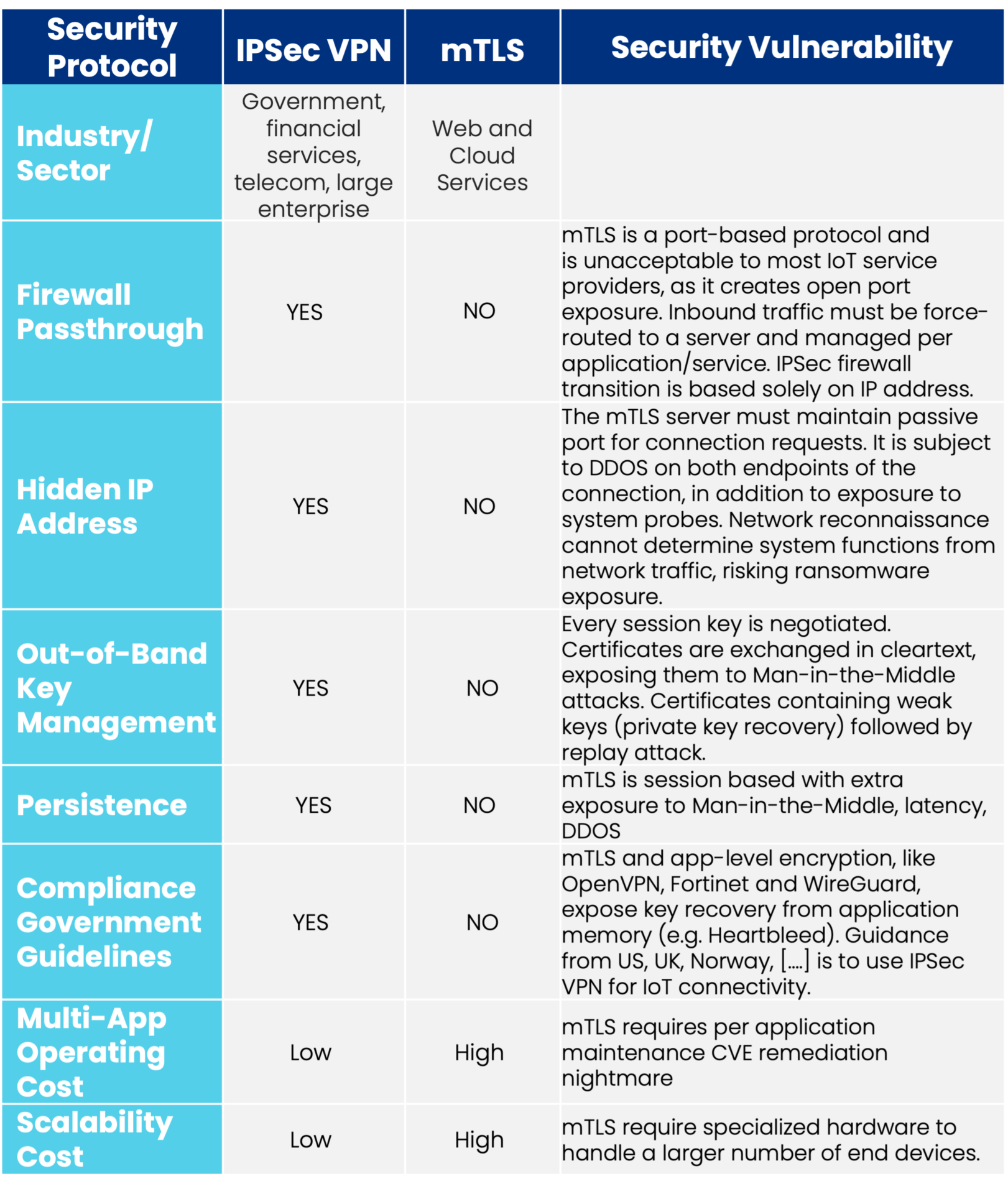
IPSec offers multiple security benefits (strongest encryption, multiple tunnels, data security and privacy, namespace tech preventing IP address visibility) and is widely used by enterprise IT for VPNs. SecEdge innovated to deliver this IPSec-based solution with cloud-based automation tools, KMS (Key Management System) and its security benefits for IoT.
See the table below:

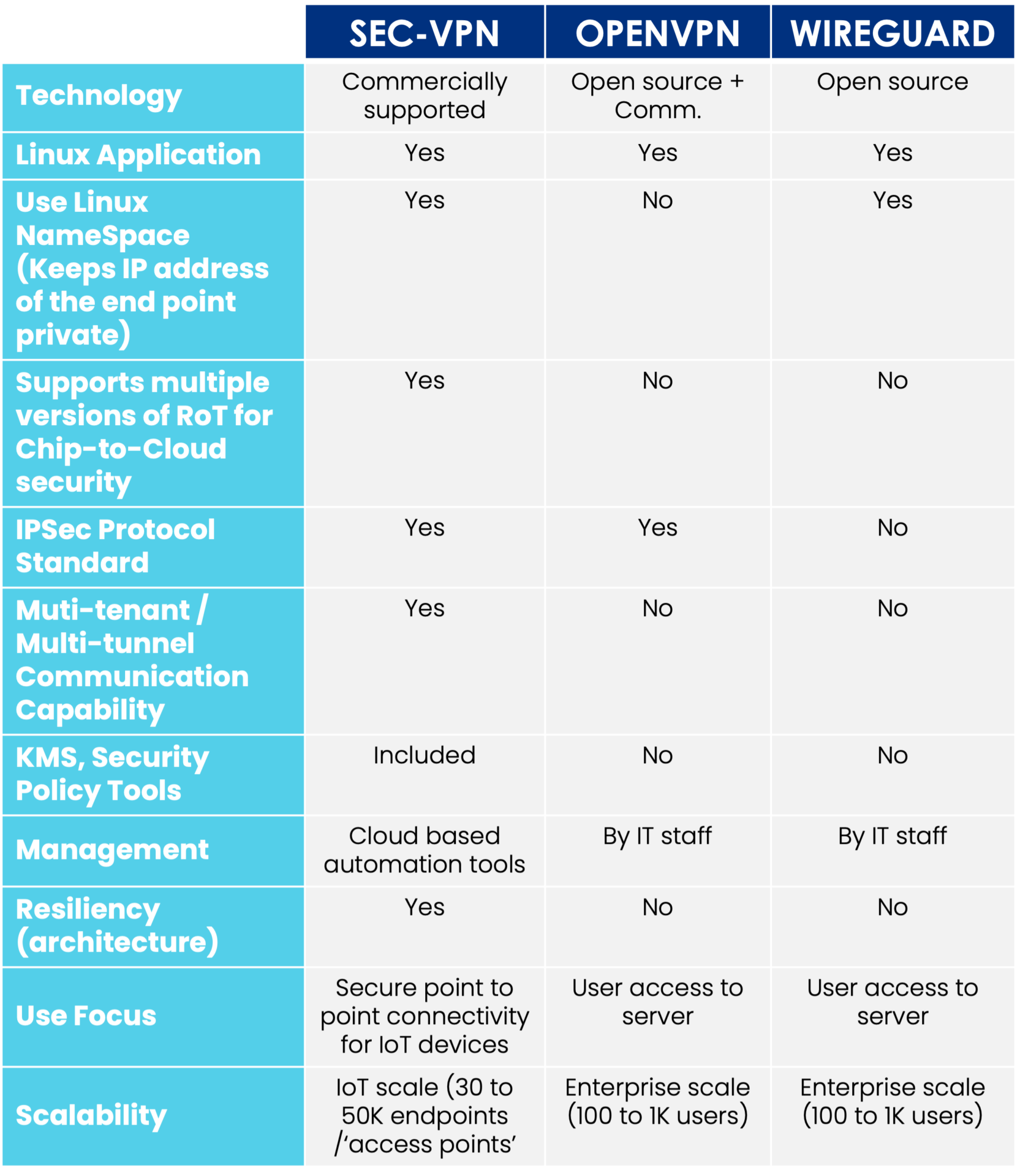
SEC-VPN™ is unique because it is designed and optimized for Edge and IoT applications. Unlike traditional IT or consumer VPN solutions, SEC-VPN includes the following in its implementation:
-
- It is “headless.” SEC-VPN does not require a user to configure an edge device for a VPN and authenticate themselves locally. This is managed centrally by ControlEdge™.
- It is multi-tenant. SEC-VPN supports multiple VPN tunnels from the device to its applications.
- It is configured for scale. With ControlEdge, all devices and applications can maintain and update their credentials in a central entity. An administrator does not need to configure each end device to recognize the credentials of its applications, or configure each application to maintain the credentials of all the devices it is communicating with. This is all managed by ControlEdge—allowing a network to scale to thousands of devices.
- It is resilient. ControlEdge can assign multiple combinations of device-to-application connections to quickly recover in the event of an endpoint failure with no administrator interaction.
We offer two options:
-
- OPTION 1: The customer hosts NetEdge™ software in their cloud (or on-premises) and MicroEdge™ is installed in their devices. SecEdge will host ControlEdge™ and give access to its services via APIs. The customer has 100 percent control over the solution and their devices. Recommended for initial deployments.
- OPTION 2: The customer hosts NetEdge software in their cloud (or on-premises) and MicroEdge is installed in their devices. The customer will host ControlEdge in their public or private data center. The customer has 100 percent control over the solution and their devices.
FAQ
EmSPARK™ Security Suite
SecEdge’s EmSPARKTM Security Suite is state-of-the-art security software that simplifies the use of advanced hardware security and reduces time to market for building more trustworthy products using our partners’ processors. EmSPARKTM simplifies implementation of the most common tasks related to securing an IoT or embedded device including:
- Trusted boot – Root of trust verified initial startup code, Linux® and other embedded firmware
- IP protection – Encryption of embedded firmware and execution of authenticated firmware
- Trusted device ID – Unique device certificate tied to root of trust for strong identity authentication
- Secure storage – Unique and encrypted storage of code and data in in-system storage
- Secure communications – Authenticate and ensure the privacy of communications to cloud devices and servers
- Secure firmware update – Remotely upgrade MPU firmware safely and securely. The Suite greatly simplifies using security features such as Arm® TrustZone®, hardware cryptography and other features
Devices secured by the EmSPARKTM Security Suite help customers reduce the risk and liability associated with IoT deployments. The Suite covers security requirements relevant at various stages of a product’s lifecycle.
We believe that a product must be secured from the time it is manufactured to the time it is decommissioned. This ensures that a company’s intellectual property (IP) is not stolen, the device operates without compromise at any point in its life, and that customer data is protected at all times. Additionally, it ensures that connections with remote systems, such as IoT cloud servers, are secure and tamper-proof.
For example, the EmSPARKTM Security Suite enables implementing a root of trust, which supports a variety of secure processes such as trusted boot. It creates a dual operating environment because our partner’s processors can switch between secure and non-secure states. This allows isolating and separating critical material and data in a hardware secured area, dramatically improving device security. Developers can easily build applications that use secure resources without having to become experts in cryptography and complex hardware security technologies.
The Suite delivers a host of capabilities, including the integration of OpenSSL with functions secured by TrustZone and preconfigured to use cryptographic functions available in our partner’s processors. The EmSPARKTM Security Suite also includes key management functions that form the basis of several secure processes such as trusted boot, storage and authentication with IoT clouds.
This allows you as the developer to focus on building the application and the device rather than spend time reading through data sheets to configure various hardware components. Result—get your products to market faster.
The EmSPARKTM Security Suite comprises the following components:
- CoreTEETM – SecEdge’s Trusted Execution Environment (TEE) for Arm® Cortex®-A based processors
- Pre-built Trusted Applications (TAs) – TAs are applications running in the secure domain (TEE). They implement critical security functions, have access to HW resources, and are used by APIs in the non-secure domain (Linux) to fulfill secure IoT use cases. The TAs included with the Suite enable access to a variety of secured resources such as the OpenSSL engine and hardware cryptography functions.
- Programming Assets in the Non-secure Domain (Linux) – Libraries and APIs enabling access to secured resources.
- Packaging Tool – A command line based utility streamlining the process of aggregating all necessary assets (bootloader, Linux components, CoreTEE, firmware, certificates and keys) needed for flashing (secure provisioning) the target device. The packaging tool ensures the proper implementation of the secure boot and root of trust enabling features such as IP protection and secure firmware upgrade.
TrustZone® is a robust, proven hardware solution for security. It is an on-chip security enclave providing hardware isolation and protection for sensitive material such as cryptographic keys, intellectual property and data. TrustZone-enabled SoCs are found in over a billion devices such as payment terminals, set-top boxes and mobile phones. TrustZone is fast becoming a standard way for IoT device makers to implement security. With TrustZone, security is designed into the product and secure functions propagated throughout the product. This results in a more secure device. It is important to note, that not all SoCs implement TrustZone the same way. This can impact your design.
For more details on the TrustZone®, please visit Arm’s website at http://www.arm.com/products/processors/technologies/trustzone.
TEE stands for Trusted Execution Environment. On top of the hardware foundation of the Arm® TrustZone® technology, the TEE adds a functional runtime environment with standards compliant APIs, strong application separation through the security focused microkernel, and strong protection of sensitive assets through access control and cryptography.
While TrustZone establishes “Normal” (non-secure) and Secure worlds, the TEE facilitates communications across these domains. Applications and functions in the Normal domain can invoke secure functions resident in the TEE through the Secure Monitor, which manages the state change from Non-secure to Secure.
The Trustzone/TEE combination enables handling sensitive data without the risking exposure. In addition, due to the integrity in the boot process, the functions provided by the TEE are less likely to be compromised by malicious code.
The TEE is also used to secure access to peripherals by implementing peripheral drivers in the TEE. This protects access to peripherals such as persistent storage, memory and displays.
Trusted Applications (TAs) are code and functions that execute only when the device is in secure state. The suite includes pre-built TAs as described above but does not allow writing custom TAs. To write custom TAs, you must obtain a license to use SecEdge’s Trusted Execution Environment—CoreTEE. A full license to CoreTEE enables greater flexibility than allowed by the security suite. To discuss this option, please [info@secedge.com] SecEdge.
There is a negligible performance impact when switching between secure and non-secure states. Switching overhead is similar to or less than that which results from a thread context switch in an operating system such as Linux.
Yes! The Suite includes procedures to load keys and certificates that enable your device to be authenticated by AWS IoT Cloud. The Evaluation Kit includes a step-by-step guide and example application to establish a TLS connection with AWS IoT (to be used with the MQTT protocol). The Suite facilitates the creation of a unique device certificate to be used for TLS mutual authentication. The Suite is cloud provider agnostic. We do not recommend any particular cloud service provider.
Read and sign the EmSPARKTM Security Suite Software Evaluation Kit License Agreement to get started on implementing advanced security for your IoT device.
License Agreement
FAQ
EmPOWER™ Lifecycle Management Platform
EmPOWER™ is a SaaS solution that provides the lifecycle management platform needed to secure, provision and update intelligent edge devices.
Together with the EmSPARK™ Security suite, EmPOWER™ enables OEM’s to actively protect their devices, business, and customers.
With EmPOWERTM, you can register devices with mutual authentication (chip and cloud), update devices securely, Gain insights into device behavior, and detect and respond to threats.
EmPOWERTM can provide registration and update services for devices that provide secure credentials like smart MCU’s, MCUs with secure elements or trusted platform modules, and smart flash. Contact us for more information.
* NOTE: NetEdge™ was formerly branded as CloudEdge™.
