SOLUTION BRIEF: PROTECTING IP AT THE EDGE

featuring EmSPARK™
Protecting Intellectual Property (AI / ML Algorithms) at the Edge with EmSPARK™ Security Suite
INTRODUCTION
THE SECeDGE™ SOLUTION
Critical applications, such as AI/ML, can be protected by housing them in a secure area with restricted access. Using Arm TrustZone™ architecture, a system-on-chip’s (SOC) memory can be partitioned into a rich (non-secure) environment and a secure environment. The rich environment is larger in memory size—typically hundreds of megabytes—and houses known (public) software, such as Linux kernels and open source supporting applications (e.g., OpenSSL). The secure environment has a small memory size—less than a megabyte—and houses the following:
- The Trusted Execution Environment (TEE) secure operating system (SecEdge’s product is called the CoreTEE™).
- Applications that need to be protected, along with applications that support the securing process (e.g., key / certificate management and secure data storage). These are known as trusted applications or TAs.
Shared memory allows access between the two environments.
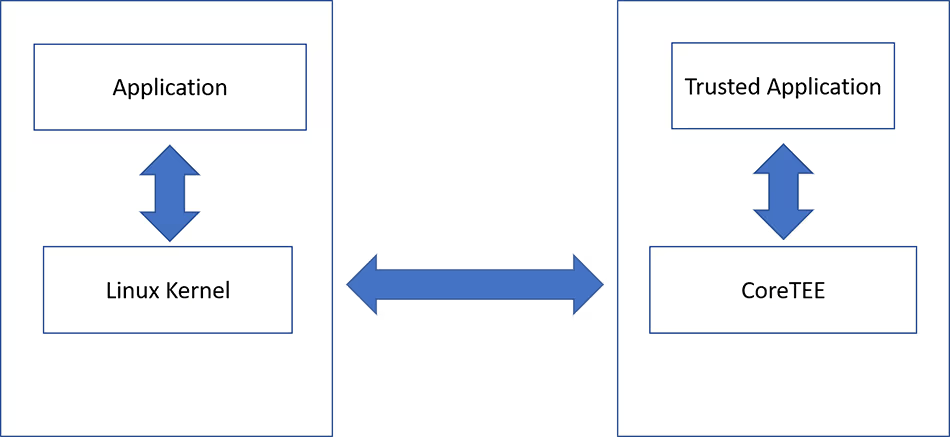
In this architecture, the secure application process works as follows:
- The IoT device’s application, running in the rich (non-secure) environment, makes a request to the Linux kernel to access the secure environment.
- The Linux kernel is suspended on one of the SoC’s cores, giving access to CoreTEE™; CoreTEE™ resumes from suspension and invokes the requested trusted application.
- CoreTEE™ accesses the non-secure memory (RAM) and acquires data through the shared memory between the two environments.
SecEdge provides four trusted applications to support the secure environment:
- Crypto TA: encryption and hashing algorithms
- Certificate Management TA: for managing credentials
- Secure Storage TA: for storing critical data in the Secure Environment
- TLS TA: secure sockets for communication with external servers
While this architecture works well for housing public applications—e.g., an open source web server—in the rich environment, an open OS, such as a Linux kernel, is often a collection of very versatile and powerful tools. This makes the OS, and its housed applications, prone to vulnerabilities. To protect a business-critical application such as an AL/ML algorithm, it is recommended that it be developed as a trusted application (TA) and housed in the secure environment.
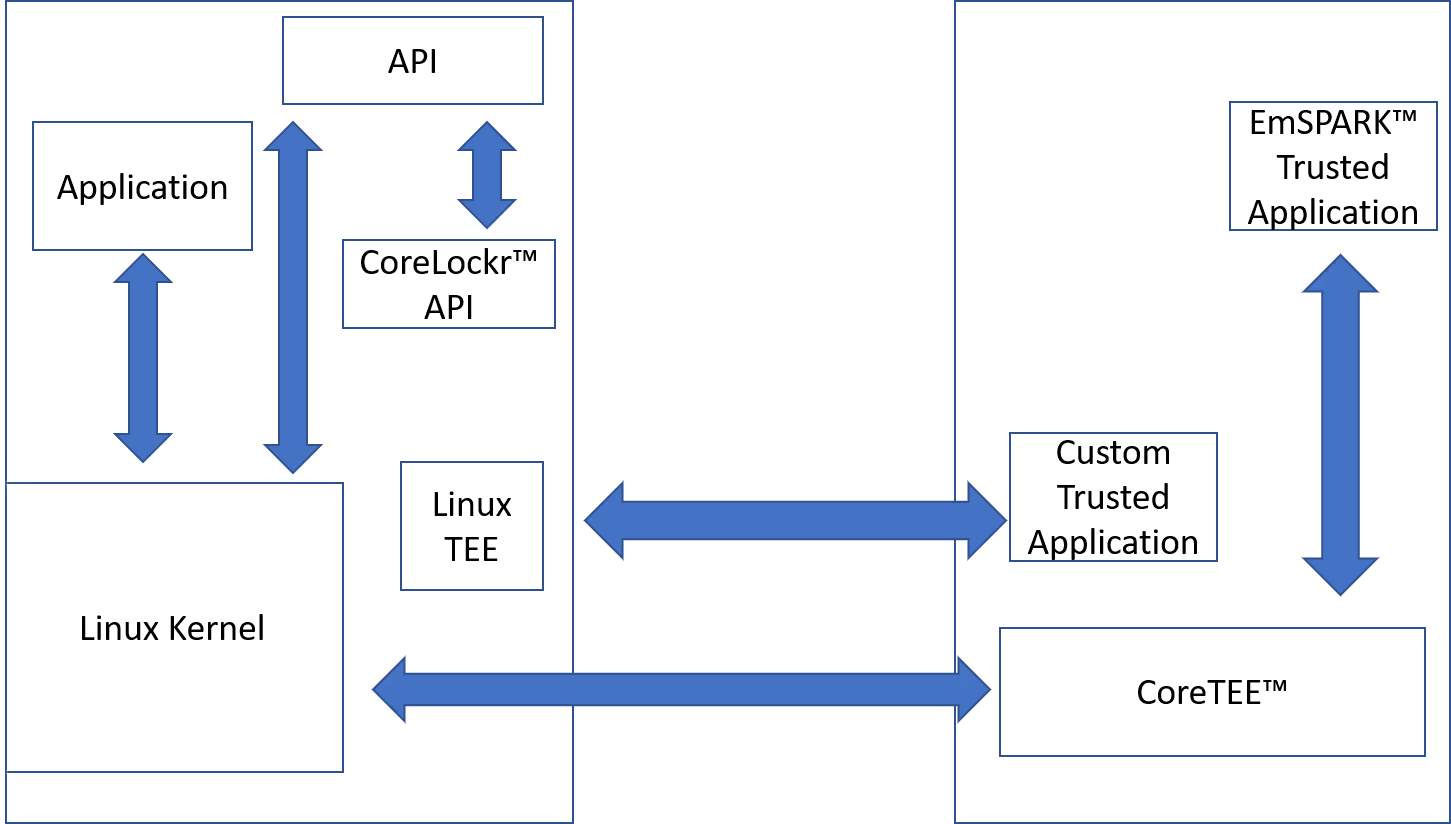
In the architecture illustrated above, both the customer’s application and the supporting trusted applications are housed in the secure environment. The customer’s application is accessed using the rich environment’s Trusted Execution Environment (TEE) interface (e.g., a Linux TEE driver). SecEdge’s trusted applications (TAs) are accessed by SecEdge’s CoreLockr™ APIs. IoT device vendors can develop trusted applications supporting their critical algorithms using SecEdge’s Software Developer’s Kit (SDK).
...theft of this kind of intellectual property can create long-term damage to a company's revenue and brand.
Download the Solution Brief
Protecting critical applications in a secure environment using SecEdge's EmSPARK™ Security Suite.
